Find and fix every single vulnerability in your web app with Secureroot’s Pentest.
Fortify Your Website Against All Potential Threats with SecureRoot’s Cutting-Edge Security Solutions.

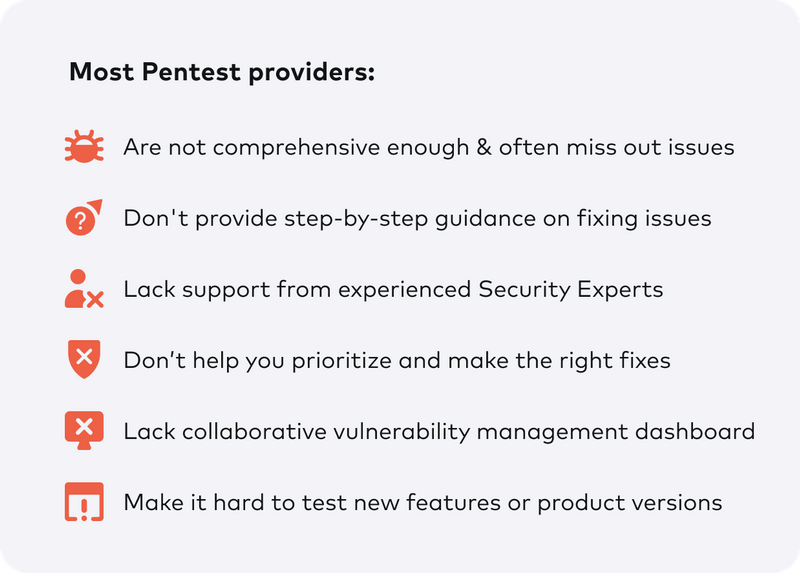
The wrong pentest partner could cost you millions, and your reputation.
In today’s digital landscape, where cyber threats are rampant, businesses must take proactive measures to protect their systems and data. One crucial aspect of cybersecurity is conducting penetration testing (pentesting) to identify vulnerabilities and weaknesses in an organization’s infrastructure. However, not all pentest partners are created equal, and choosing the wrong one can have severe consequences, including financial losses and damage to your reputation.
No other Pentest product combines automated scanning + expert guidance like we do.

Industry-leading continous vulnerability scanner


Industry-leading continous vulnerability scanner
Secure your website and find vulnerabilities that other pentests often miss
- Goes beyond surface-level testing, utilizing a wide range of testing methodologies to uncover vulnerabilities.
- Stays at the forefront of the cybersecurity landscape, constantly researching and developing advanced exploitation techniques.
- simulating real-world attack scenarios identify vulnerabilities that other pentests often miss.
- Our pentest service includes a deep analysis of your unique codebase, ensuring that no vulnerabilities go unnoticed.
- Takes a comprehensive approach to threat modeling, considering all potential attack vectors specific to your web app.
- We Provides comprehensive reports detailing the identified vulnerabilities, their potential impact, and recommended mitigation strategies.


Get ISO, SOC2, GDPR, CIS compliance-ready without the hassle.
With SecureRoot’s comprehensive testing engine, you can quickly achieve compliance and secure your cloud infrastructure, including ISO 27001, HIPAA, SOC2, and GDPR. Your systems will be thoroughly protected without the hassle of managing multiple tools or vendors. SecureRoot helps you stay compliant with industry standards and protect your reputation.
Get your web app tested for 3000+ different vulnerabilities and hacks.

Vulnerability Assessment & Penetration Testing (VAPT)
We analyze your cloud infrastructure for any misconfigurations that could allow malicious users to access your system and damage your reputation and customer's trust. We’ll cover all major security standards including CIS, CSA, OWASP, SANS, CERT, CREST, SOC2, ISO27001 etc.

Server Infrastructure Testing & DevOps
Scan existing configurations, ensure encryption & safe data storage, optimize DevOps processes and make sure your data never gets breached.

Network Devices Configuration
We'll assess the device patch level, logging & auditing implementation, authentication mechanisms & run tests based on device configuration, administrative and authentication services, network filtering, protocol analysis.
Vulnerability Assessment & Penetration Testing (VAPT)
We analyze your cloud infrastructure for any misconfigurations that could allow malicious users to access your system and damage your reputation and customer's trust. We’ll cover all major security standards including CIS, CSA, OWASP, SANS, CERT, CREST, SOC2, ISO27001 etc.

Server Infrastructure Testing & DevOps
Scan existing configurations, ensure encryption & safe data storage, optimize DevOps processes and make sure your data never gets breached.

Network Devices Configuration
We'll assess the device patch level, logging & auditing implementation, authentication mechanisms & run tests based on device configuration, administrative and authentication services, network filtering, protocol analysis.