Secure Your Network Infrastrucutre from Vulnerabilities and Exploits with SecureRoot Pentest Service
The wrong pentest partner could cost you millions, and your reputation.
Choosing the wrong pentest partner can have severe repercussions, including financial losses and damage to your organization’s reputation. At SecureRoot Risk Advisory, we prioritize your business’s security by providing expert pentesting services tailored to your specific needs. Our team of skilled professionals, comprehensive testing approach, transparent reporting, and commitment to confidentiality make us the ideal partner to safeguard your assets and reputation. Contact us today to discuss how we can help strengthen your organization’s security defenses and ensure a safer digital future.
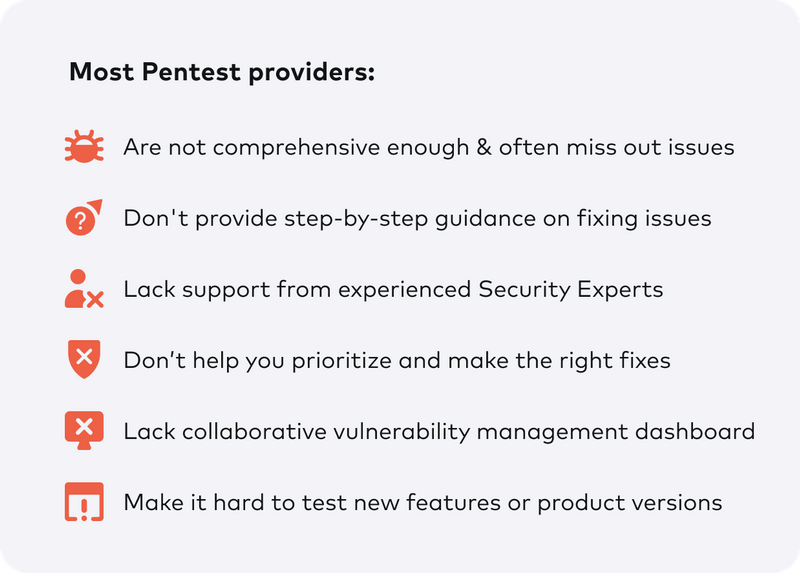
Stay Ahead of Cyber Threats with Comprehensive Cyber Security Solutions from SecureRoot

Industry-leading continous vulnerability scanner

Industry-leading continous vulnerability scanner
Bulletproof Your Network: Uncover Overlooked Vulnerabilities and Exploits with Our Comprehensive Pentesting Services.
- We specialize in providing top-tier pentesting services that allow you to bulletproof your network.
- Our pentesting services leave no stone unturned, meticulously examining every facet of your network infrastructure.
- Our experts meticulously analyze your systems, applications, and networks to identify weaknesses that could be exploited by attackers.
- From misconfigurations and weak passwords to unpatched software and social engineering vulnerabilities, we assess the full spectrum of potential threats.
- Our pentesting process encompasses a comprehensive range of assessments to ensure that every aspect of your network is thoroughly evaluated.
- Our experts simulate attacks from outside your network perimeter, mimicking the techniques used by external hackers to gain unauthorized access.
- We delve deep into your internal network to assess the security posture of your internal systems, servers, and workstations.
- We assess the security of your wireless network infrastructure, identifying any weaknesses in encryption, authentication, or access control.
- We provide you with detailed reports that outline the discovered weaknesses, their potential impact, and actionable recommendations for remediation.
Get clear, actionable steps to patch every issue and work together seamlessly.
- Our team of highly skilled and certified security experts will conduct a thorough examination of your network and infrastructure.
- Leveraging industry-leading tools and methodologies, we will simulate real-world cyber attacks to test the resilience of your systems.
- We will provide you with a comprehensive report that highlights all identified vulnerabilities, along with their potential impact on your organization.
- We will assist you in implementing a structured approach to ensure that patches are applied promptly and efficiently, reducing the window of opportunity for potential attackers.
- Our experts will collaborate with your team to address any questions or concerns and provide training sessions tailored to your organization's needs.
- We offer ongoing support and monitoring services to ensure that your systems remain secure over time.
Ensure Your Network Infrastructure Compliance with ISO 27001, SOC2, GDPR, and CIS Standards Hassle-Free!
At SecureRoot, we understand the challenges businesses face in meeting various regulatory requirements and security standards. Our expert team is dedicated to helping you navigate through the complexities of these frameworks and achieve full compliance without the usual hassles.
Partnering with SecureRoot Risk Advisory means you’ll receive tailored solutions that fit your specific business needs. We work closely with your team, providing expert guidance and support at every step of the compliance journey.
Contact SecureRoot today, and let us simplify the compliance process for your network infrastructure, ensuring it meets ISO 27001, SOC2, GDPR, and CIS standards with ease. Focus on your core business, and leave the compliance worries to us!
Get your web app tested for 3000+ different vulnerabilities and hacks.

Vulnerability Assessment & Penetration Testing (VAPT)
We analyze your Network infrastructure for any misconfigurations that could allow malicious users to access your system and damage your reputation and customer's trust. We’ll cover all major security standards including CIS, CSA, OWASP, SANS, CERT, CREST, SOC2, ISO27001 etc

Server Infrastructure Testing & DevOps
Scan existing configurations, ensure encryption & safe data storage, optimize DevOps processes and make sure your data never gets breached.
Network Devices Configuration
We'll assess the device patch level, logging & auditing implementation, authentication mechanisms & run tests based on device configuration, administrative and authentication services, network filtering, protocol analysis.